
Data Privacy – What it means for your business?
What is Data Privacy?
Data privacy relates to how information or data should be held or stored by organisations. Data privacy involves setting up data access controls, getting data consent from data subjects and maintaining data integrity in compliance with data protection laws. For businesses, data privacy goes beyond securing PII (Publicly Identifiable Information) of its employees and customers but also securing its IP, financial information, proprietary research & development.
Why is Data Privacy so critical now?
Data is considered as the new oil that is driving the exponential growth of enterprise and consumer data. Disruptive business models driven by new technologies are enabling businesses to collect, store, exchange and analyze data to enhance customer experience (CX). Exponential growth in data also means increasing instances of data breaches, thereby detecting and preventing them have become the key priority for businesses. Accidental or intentional data breaches often lead to significant reputational damage, including financial losses but also negatively impact the stability and credibility of the businesses.

One of the most important data protection legislation enacted till date is the General Data Protection Regulation (GDPR) which directs collection, use, transmission of data collected. With the advent of GDPR, many other countries have introduced new data privacy laws, while others are reviewing their existing regulations. The ever-increasing data compliance requirements across a number of countries is likely to enforce businesses to comply with the law of the land, thereby creating a unique set of challenges to control personal data irrespective of the location where it is being collected stored, shared and processed empowering the business take ownership of the data while imposing harsh penalties for non-compliance.
How can businesses comply with GDPR and protect their data?
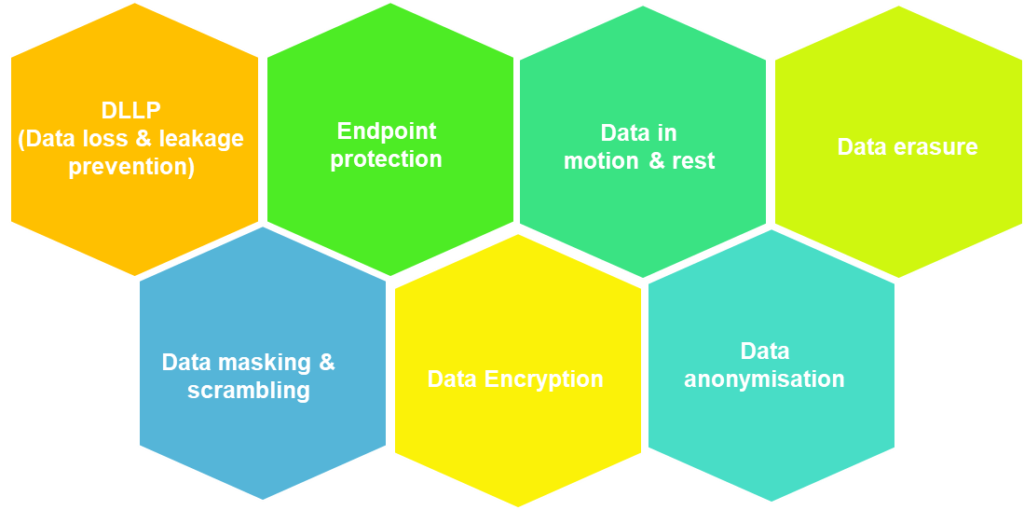
Securing PII and other confidential data from malicious attacks is an utmost priority for any business irrespective of the size. For prevention of data breaches and protecting data, a myriad of storage and management options can help businesses anticipate, respond, and react to threats. Some of the most commonly used practices and technologies include:
DLLP (Data loss & leakage prevention): Data loss prevention includes tools and technologies that businesses can use to prevent data from accidentally being deleted, lost or stolen which includes prevention from access and misuse by unauthored users. DLP solutions monitor critical data flows for businesses like end points, cloud, mobile devices including filter data streams on networks. DLP solutions can also identify areas of weakness, variance for forensics, adhere to audit and compliance requirements. Data leakage prevention solutions prevent data transmitting to someone outside the organization which minimize breaches.
Data Encryption: Data encryption renders data into a form or a code, so that only intended users with access to decryption key or password can read it. Currently encryption is one of the most popular and effective data security method used by businesses. The primary purpose of data encryption is to safeguard digital data privacy stored or transmitted using internet or any network as it is stored on computer systems and transmitted using the internet or other computer networks.
Data masking & scrambling: Data masking is the process of creating a structurally similar but simulated version of an organization’s data. In data masking, the data may be altered in a number of ways, including encryption, character shuffling, and character or word substitution. Data scrambling involves removal of sensitive data for data confidentiality. Irrespective of the method chosen, the data in both these methods is altered in a way or the other that makes reverse engineering impossible.
Data anonymisation: Data anonymisation techniques modify data across systems so it cannot be referenced back to a specific individual, while retaining the data formats and source integrity. Once data is truly anonymised and individuals are no longer identifiable, the data will not fall within the scope of the GDPR and it becomes easier to use for any business
Data in motion & rest: Data in motion, refers to data actively moving from one location to while Data at rest is data stored in ways that is not actively moving from device to device or network to network. Securing data at rest is relatively easier than securing data in use while attackers often find data at rest a more valuable target than data in motion. The risk profile for data in transit or data at rest depends on the security measures that are in place to secure data in either state.
Endpoint protection: Endpoint protection relates to the protection of endpoints, or end-user devices such as PCs, laptops, POS (Point of Sale) systems, tablets, servers, and mobile phones. Endpoints provide access to corporate and private networks to establish points of entry that security threats can exploit. The perilous question surrounding endpoints is that they characterize one of the key areas of vulnerability for businesses and can be an easy entry point for cybercriminals.
Data erasure: Data Erasure is a software & hardware solution of overwriting to completely destroy all electronic data on hard disk or any other digital media. Data erasure limits the liability by deleting data that is no longer needed. Data erasure can be done after the data has been processed or analyzed or no longer relevant for the business. Data erasure is also one of the primary requirements of many compliance laws such as GDPR.
With businesses embracing rapid digitalization, the spurt in user and enterprise driven data is compelling businesses to adopt a privacy first culture. The need to safeguard “data assets” has become a key priority for businesses irrespective of their size. CyberSophy helps businesses protect their data in a rapidly evolving environment while remediate evolving threats, analyze risk and lead data governance efforts to develop a framework for an ongoing data privacy compliance. To help you find the right data privacy solution for your organization and request a demo, contact us at info@cybersophy.net.



